SPECIAL SERIES: A conversation with former CIA cyber chief Kevin Zerrusen and David Lawrence, founder of risk intelligence firm RANE
June 7, 2022

SPECIAL SERIES: A conversation with former CIA cyber chief Kevin Zerrusen and David Lawrence, founder of risk intelligence firm RANE
Last month, Costa Rica was forced to declare a state of national emergency similar to those reserved for disasters. The culprit: ransomware attacks. The notorious Conti ransomware group began hacking the country in April, disrupting its finance ministry and other government agencies, according to the FBI. The gang first demanded a ransom of $10 million, but reportedly raised it to $20 million to restore access to data. The attack affected 27 government institutions, including state-run utilities.
Ransomware is the number one cybersecurity threat today, according to the National Cyber Security Centre of the U.K. In this type of attack, the hacker releases malware to encrypt data and make it inaccessible until a ransom is paid. To discuss this and other cyber threats, Mukul Pandya, former senior fellow at Wharton’s AI for Business program, spoke with David Lawrence, founder and chief collaborative officer of risk intelligence company RANE, and Kevin Zerrusen, COO of Reality Defender, which has developed an enterprise-grade deepfake detection platform.
Lawrence had been the associate general counsel and managing director at Goldman Sachs, where he formed and was the global head of the Business Intelligence Group. Before that he was an assistant U.S. Attorney in the Southern District of New York. Zerrusen is the former senior advisor for cybersecurity policy to the Securities and Exchange Commission. He also previously led the Cyber Center of the Central Intelligence Agency.
An edited transcript of the conversation appears below.
Mukul Pandya: What are the top three cybersecurity threats companies face today? What's keeping chief information and security officers up at night in 2022?
Kevin Zerrusen: The number one cybersecurity threat today is ransomware. This is a threat that emerged two or three years ago and just continues to increase in terms of volume and severity of attacks. There are several reasons for that − some of it has to do with how the attackers have evolved the use of ransomware over the last few years − and they are continuing to learn as they move forward.
When it started, for most of the attacks the idea was to simply get into the network, encrypt it and then demand a ransom. When (hackers) figured out that companies were relying on backups and were not as willing to pay the ransom, they started to exfiltrate the data first and then encrypt. If you're an organization that prides itself on the ability to keep the data to yourself, having the data leave the organization is probably more severe than the actual disruption from a ransomware attack, which is the need to rebuild the network and system.
What you see today is those attacks are continuing and they're more targeted. The attackers are looking for the organizations that have the capacity to pay millions, if not tens of millions of dollars in terms of ransom, and desire to protect data as well as their operational viability.
Figure 3: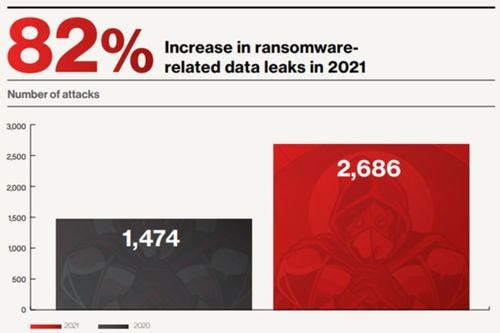 Source: 2022 Global Threat Report from CrowdStrike
Source: 2022 Global Threat Report from CrowdStrike
For me, that's the number one threat. And then after that is cloud security because there is a tremendous move by virtually all organizations to the cloud. … There's lots of positive aspects of being in the cloud. In addition to your own protections you have the protections that are afforded by the cloud provider. But you still have to configure things right. You need to understand where your responsibilities lie, and where the cloud providers’ responsibilities lie and if you don't constantly maintain access and identity access management controls, you'll lose the benefits of the move to the cloud. That's a huge risk for organizations.
The last one is insiders. These can be malicious insiders who are determined to harm the organization for a specific purpose. They're vengeful, or they're unhappy with something. But then you also have insiders who are just careless folks that click on the attachment or click on the link and become victim to numerous types of ploys by the cyber actors, which then provides an opening for either loss of data or disruption of the network.
David Lawrence: We don't yet have a systemic answer to cybersecurity issues. We continue to innovate with products, offerings, and platforms. We market the advantages of connectivity, efficiencies of being online, what the data aggregation provides, but only as an afterthought we think about security. …
The notion of hijacking something inside a company whether it's proprietary secrets, or even executives, is nothing new. And indeed, the actors are also very familiar and I would argue go back to biblical days − individual criminals, loosely organized criminal groups, organized crime groups, but they're also state actors and the state sponsored ones. Unfortunately, companies are largely − not entirely − left to fend for themselves.
Pandya: How fast is ransomware growing? What are the emerging kinds of ransomware attacks for which companies should be prepared?
Zerrusen: It's pervasive and it's increasing. It's increasing because most of the victims are paying the ransom. They're paying it because maybe their operations depend on being online all the time and they can't afford to be offline. There are other organizations that would be willing to take the hit in terms of being operationally disabled or disrupted for a while.
The reason that they pay the ransom is because they can't afford to lose the data. The attackers know this. They're purposefully looking for companies that, first of all, are going to be able to pay a hefty ransom. And sometimes the attackers are in for days, weeks, months, before the attack actually occurs. In some cases, they're actually looking for the company's insurance policy. How big it is − and then they'll ask for that in terms of the ransom because insurance companies have been paying. That might change going forward.
But in the past, most companies have been willing to pay the ransom because they have insurance. So as long as you have a situation where the companies are paying and the attackers can take advantage of that, … it’s going to just continue into the future. Most of these attackers are not using sophisticated means to target organizations. They're using flaws that exist in the network – a vulnerability that wasn't patched or a software program that wasn't updated, or somebody's clicking on the email they shouldn't have been clicking on … or typing in their credentials when they shouldn't be doing so. It's not as if the attacker has to work really hard to do this.
So you're going to just continue to see these kinds of attacks until it gets to a place where the organizations figure out how to keep these attackers out. As companies think about the future, they should have a plan on how they're going to deal with a ransomware attack. They should practice (the plan), and they should have a methodology for making decisions about whether they're going to pay or not.
Lawrence: Jim Comey when he was director of the FBI said there are only three kinds of companies left in this world − those who have been hacked, those who are about to be hacked and those who have been hacked and don’t know it. Kevin has been an evangelist about the importance of early detection. … Think of this in terms of the defense. It's basically risk mitigation.
Let's go back to physical kidnapping. Some of the same core gamesmanship goes on − if we pay the ransom he won't be released, and if I pay the ransom it will encourage them to target other executives. … Then you have issues around ransom drops. It's not the cash or the suitcase on the side of the road. Very often, if not almost exclusively, payments are in Bitcoin or some other digital coins. Then, do we report this to the authorities? Many of these ransomware attacks begin with the admonition that if you bring law enforcement in, you'll never see your data again. …
Figure 1: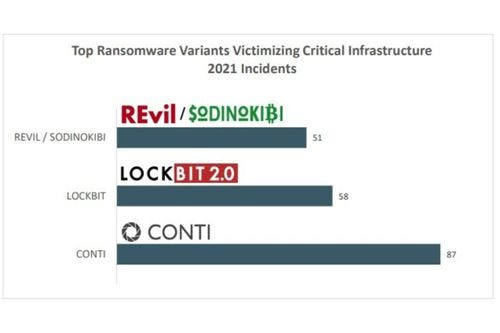 Image credit: FBI Internet Crime Report 2021
Image credit: FBI Internet Crime Report 2021
It's interesting because the ransom that is being assessed … very often from a corporate standpoint, it's immaterial. Not that it's not an insignificant amount, but from a cost benefit standpoint, it's immaterial if they actually can get their data back.
Zerrusen: You need to have thought through how you're going to deal with a ransomware attack and maybe even need a playbook. You certainly need to exercise the scenario of a ransomware attack and … make a decision to pay or not pay. If you're going to pay, decide how you are going to do it, which is probably in cryptocurrency or something.
Lawrence: People think of ransomware in terms of data that they need for their day to day operations, or maybe confidentiality, protecting a business plan, customer list or whatever. … They (may) have sensitive information that could be embarrassing (and brings about) the ability to blackmail. It can cause all sorts of direct and indirect consequential damages.
Pandya: I’m glad both of you mentioned crypto and blockchain because these technologies are compelling finance to become more decentralized. How do you think that affects cyber risk in the finance industry? What should companies in this field be thinking about and what actions should be taken today to protect their security?
Zerrusen: For many organizations, start with the basics. Understand the risks that your organization faces. Knowing simple things like − what is it that we have to protect? What are our critical assets to hold on to and how are those protected? Are we protecting them completely and fully?
Make sure that … your vulnerabilities have been patched, your systems have been updated, that your identity and access are tightly controlled and you have policies and procedures and governance in place to do all these things. And you’re using real data to know how well or not your system and controls are performing.
There are going to be attacks like the Solar Winds attack, which was a supply chain operation that nobody else had seen before. But most of the attacks that are happening on our systems are because somebody clicked on the wrong thing, somebody forwarded something, somebody didn’t update software, somebody didn’t investigate this, or take proper steps.
So I think that for most organizations, if they could just manage the basics, that would be enormously helpful and beneficial, because you want to make it as hard as possible for the attacker. Not because you'll stop them from attacking, but they'll go someplace else.
All of the attackers in these nation states, they’re criminal, they have no bosses, they have no budgets, they don’t have requirements that they have to maintain so they’re going to try to accomplish their objectives as quickly and efficiently and as cheaply as they possibly can. And if you’re too hard to attack because you’ve done the basics, and somebody else hasn’t, they’re going to go someplace else. Unless they’ve decided you’re the only target that they want, then you’re probably out of luck. Once you’ve done the basics, then you can begin to add other things.
Figure 2: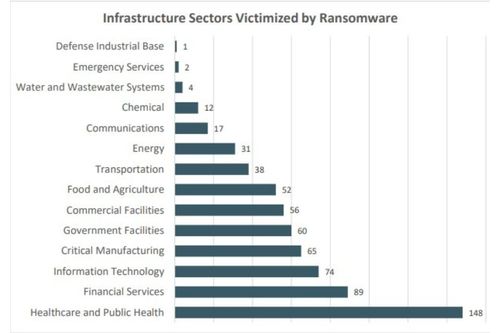 Image credit: FBI Internet Crime Report 2021
Image credit: FBI Internet Crime Report 2021
You mentioned cryptocurrency – obviously that’s a big issue. It’s probably game-changing. (However,) the biggest concern I have is the evolution of quantum computing. If an organization’s systems rely upon encryption to protect the infrastructure, to protect the users, and those systems can be attacked or broken with quantum computing, that's a huge risk. The United States is not leading in quantum computing, in research and development. We need to really think about how that will impact the future.
If you talk to organizations that are thinking about and involved in this, they'll say, ‘how can I make encryption quantum proof?’ That’s possible but it's probably not doable on the scale that it needs to be done, and it's not going to be cheap.
Pandya: I would love to ask you both about deep fakes. Historically, they've been seen as a political problem because they amplify misinformation. But I wonder if you see deep fakes as a serious threat in the business world. What major risks do companies face in this regard? Would you be able to give any examples of deep fake threats in business and how these are being addressed?
Lawrence: It’s so important for people to understand the term deep fakes and what it is and what it likely is going to become. Kevin recently retired to address the deepfake issue, which speaks volumes as to the imminent nature of this threat and the importance of getting really smart people to pay attention to this.
Zerrusen: The deep fakes disinformation is really an assault on truth. We should all be concerned about that. Because one of the challenges that we are facing is that it's very hard to have a conversation and to sort things out, if there are different interpretations of the truth, or the truth is different for one person versus another versus another.
This disinformation has been around since the beginning of time. Deep fake is another iteration of that, I suppose, and … criminals have used disinformation to advance their purposes in one form or another.
Related stories:
Cybersecurity survey: 80% of companies globally hit by ransomware attack
Cardiologist moonlights as ransomware mastermind
Ransomware deals death blow to historic US college
'Robin Hood' ransomware forces victims to do good
But deep fakes take disinformation yet to another level because it is very difficult, with some of the technologies that now exist, to distinguish between real or fake. And, in fact, there have been some surveys and studies that suggest that people are more inclined to believe a deepfake than they are to believe reality. The technology has gotten that good.
Some of the fakes are kind of fun. Folks in the entertainment industry love the opportunities to create lifelike avatars. There's lots of good aspects of this technology, but there's some very dangerous and sinister ones as well. People's lives, people's reputations and an assault on democratic principles can happen with deep fakes.
Deep fakes come in lots of different types. It's pretty easy to do − anybody with a 10-year old iPhone can make a deep fake. For every 1,000 producers of deep fakes or individuals working on creating deep fakes there's probably three or four that are working on the detection or the defensive side of that. So it's really kind of skewed in favor of creation.
If you haven't seen what I'm talking about, you can go to ThisPersonDoesNot Exist.com. Click on it and there will be a face that looks like a photograph of a real person but the person doesn't exist. Click it again, it's a completely different person, but it looks like it's real.
And then there’s audio too. For some organizations, particularly the financial sector, the audio might be the most dangerous. With some of the best technology that exists there, you only need a few seconds of someone's real voice to actually replicate it synthetically.
There have been instances where the “CEO” has called the chief financial officer to wire $5 million or $10 million or $20 million to this bank account, and it was fraudsters. A lot of the protection that we have today has to do with voice recognition -- if that becomes degraded in some fashion that poses a challenge.
Another challenge is the Help Desk and social engineering attempts. These happen all the time and you can do it in real time. The help desk person doesn't know that they're not talking to a real person, which presents a huge threat.
The challenge is can we develop the mechanisms, the technologies that will help us distinguish truth from falsehood.
You May Also Like
.jpg?width=700&auto=webp&quality=80&disable=upscale)
.jpg?width=700&auto=webp&quality=80&disable=upscale)
.jpg?width=700&auto=webp&quality=80&disable=upscale)
.jpg?width=300&auto=webp&quality=80&disable=upscale)
.jpg?width=300&auto=webp&quality=80&disable=upscale)
.jpg?width=300&auto=webp&quality=80&disable=upscale)

