
The FBI, along with German and Dutch law enforcement officials, has dismantled the operations of a major ransomware group that has held hostage the computer data of thousands of victims around the world.
The U.S. Justice Department said the Hive ransomware group has targeted more than 1,500 victims in more than 80 countries, including hospitals, schools, financial firms and critical infrastructure such as government facilities. In total, Hive had pocketed more than $100 million in ransom.
Since last July, the FBI has been infiltrating the computer networks of Hive and seized 300 decryption keys to give to victims so they can regain access to their data without having to pay a ransom. The FBI also distributed at least another 1,000 decryption keys to past victims.
The DOJ estimates that the FBI saved victims from having to pay $130 million in ransom to Hive.
In an attack, hackers use ransomware, a form of malware, to encrypt the computer files and applications of an individual or organization and demand a ransom to decrypt them. This malware can enter a computer system through system vulnerabilities and phishing emails that entice people to click on them and thus download the malware, among other means.
One hospital that fell victim to Hive had to use analog methods to treat patients and could not accept new patients, the DOJ said.
The FBI worked with the German Federal Criminal Police and Reutlingen Police Headquarters – CID Esslingen, and the Netherlands National High Tech Crime Unit to bust the Hive syndicate.
Cyber-organized crime
Hive ran a business that offered ransomware-as-a-service. Administrators or developers created and maintained the malware while affiliates or recruits mounted the attack.
Victims often suffered a double whammy: Not only did they have to pay a ransom to get access to their files back, their data would be stolen and so they had to pay another ransom for their files not to be released publicly.
The ransom is split 20% for administrators and 80% for affiliates.
Hive gains access to victims’ networks through single-factor logins via Remote Desktop Protocol (RDP), virtual private networks (VPNs) and other remote network connection protocols. It also made use of phishing emails with malicious attachments and exploited FortiToken vulnerabilities.
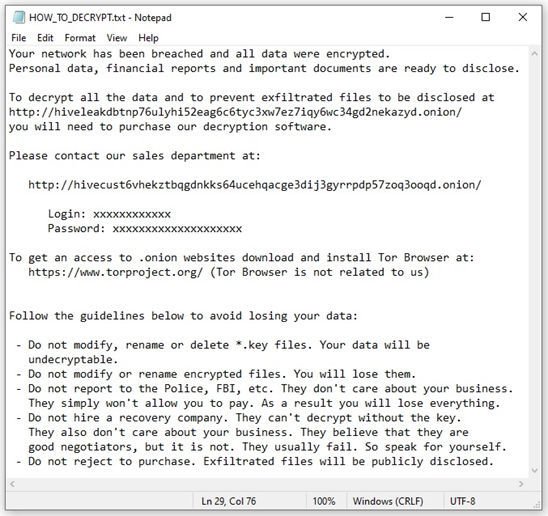
Sample of a Hive ransom note
About the Author(s)
You May Also Like


.jpg?width=700&auto=webp&quality=80&disable=upscale)
.jpg?width=700&auto=webp&quality=80&disable=upscale)
.jpg?width=700&auto=webp&quality=80&disable=upscale)


.jpg?width=300&auto=webp&quality=80&disable=upscale)

.jpg?width=300&auto=webp&quality=80&disable=upscale)