Carnegie Mellon researchers invent a system to find hidden cameras.
June 22, 2022

Carnegie Mellon researchers invent a system to find hidden cameras.
Worried about hidden cameras in your hotel room or Airbnb? Researchers at Carnegie Mellon University developed a system to find these invasive devices in unfamiliar, untrusted environments.
The Lumos System lets users detect these Wi-Fi-connected IoT snooping devices in a physical environment using only handheld devices such as a smartphone, according to a paper by university researchers. It was accurate 95% of the time.
Lumos uses an AR interface to find and identify hidden cameras. The system looks for encrypted wireless packets being transmitted as the user uses a detection device to pace around the area. The researchers used a 2-bedroom, 1,000 square-foot apartment as their test environment.
Figure 1: 
Lumos’ localization module utilizes signal strength measurements found in 802.11 packets, also known as Received Signal Strength Indicators (RSSI). The user’s relative position to the cameras is measured by the visual inertial odometry (VIO) information.
On an Apple iOS device, ARKit, a developer API, created an AR interface by utilizing the mobile device’s camera, motion sensors, GPU, and CPU. The position of the user is also tracked.
Figure 2: 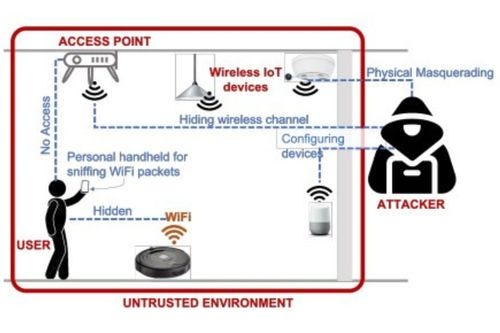
"As the user walks closer to each device, the RSSI values corresponding to those data points increase and then reduce as she walks away from the device. Lumos leverages the spatial measurements of RSSI values and their variations to estimate the location of each device," the researchers explained in their paper.
It doesn’t matter how fast or slow a user walks around to look for the devices.
Lumos also has a fingerprinting module that uses a machine learning model to recognize the devices based on MAC addresses.
The scientists studied 44 IoT devices of all makes and models in six different scenarios. However, one possible flaw is that a sophisticated hacker can change the devices’ signal strength or deploy MAC address randomization techniques to hide their devices.
You May Also Like
.jpg?width=700&auto=webp&quality=80&disable=upscale)
.jpg?width=700&auto=webp&quality=80&disable=upscale)
.jpg?width=700&auto=webp&quality=80&disable=upscale)


.jpg?width=300&auto=webp&quality=80&disable=upscale)

.jpg?width=300&auto=webp&quality=80&disable=upscale)