January 31, 2020

by Avesta Hojjati, DigiCert
31 January 2020
The IoT has not yet reached maturity, but in all the excitement users and manufacturers enthusiastically acquired and invested in it without properly considering security. We know that story.
We’re still figuring out a lot about the IoT: What we want from it, what level of privacy we are comfortable with, where the legal limits should lie and how to secure it. We haven’t quite figured out the answers to all of those questions yet but getting them is a race against time.
The issue goes beyond mere data theft. Attackers can now leverage the functionality of the IoT to further their crimes.
Issues have been raised with robotic vacuum cleaners which scan the architecture of a house in order to determine the area they have to clean. This would be a great feature if it weren’t for the fact that it uses a default username/password combination, allowing an adversary to turn that device into a remote spying device. It’s just one example of many. In recent research conducted by Kumar et. al. “All Things Considered: An Analysis of IoT Devices on Home Networks”, researchers identified that in 11 different geographical locations and amongst 15.5 million homes, there exist 83 million IoT devices.
Figure below depicts IoT device type distributions between different geographic regions.
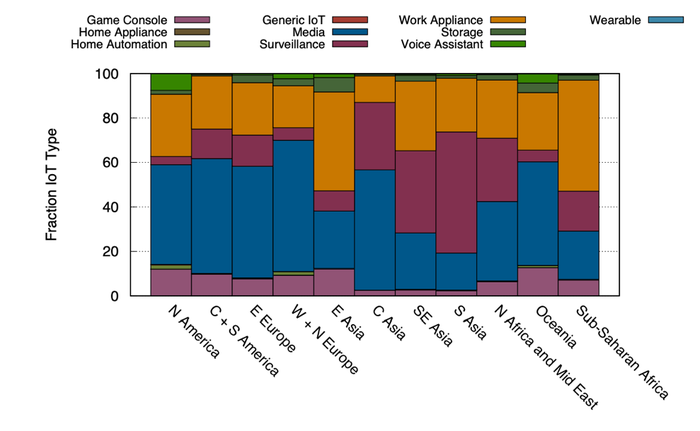
Source: Kumar, Deepak, et al. "All things considered: an analysis of IoT devices on home networks." 28th {USENIX} Security Symposium ({USENIX} Security 19)
It feels as though people are wising up to these threats. Governments are introducing regulation all over the world at both regional and national levels. California’s SB-327 law comes into force in January, which compels manufacturers to rid their devices of the all too common problems of default passwords. The Japanese Government are also drawing up plans to regulate the IoT this year.
The UK Government recently introduced a certification scheme which will allow compliant devices to be labeled with the Secure By Design standard. This move could place security as a competitive differentiator when enterprises and home users purchase IoT devices. The Finnish Government have recently announced that they will be adopting similar measures. It seems that market forces will now help police the security of the IoT, too.
It might take a while for the full force of that regulation to be felt. Hopefully, industry will take responsible action and continue to build good security into IoT devices. Maybe we should be asking how to remove those inevitable vulnerabilities from our concern.
We’re still figuring out what we want from the IoT, what data we’re going to let it collect and with what level of autonomy they’re going to use that collected data. It’s from that perspective that it makes sense to adopt security practices which can learn and grow with it.
Artificial Intelligence could help here. With AI we can start not just to stop threats, but predict them. In the case of the IoT, we can construct technologies which will not only be able to spot malicious, infected IoT devices within a given network but be able to accurately predict which devices will be malicious in the future or in danger of getting comprised. The table below categorizes Machine Learning based IoT security methods.

Source: Xiao, Liang, et al. "IoT security techniques based on machine learning." arXiv preprint arXiv:1801.06275 (2018)
By collecting data from a variety of devices over time we can identify patterns. We can evaluate outdated operating systems, default passwords, vulnerable libraries, a lack of authentication, encryption and signing - all factors which contribute to the devices vulnerability. Those factors on their own cannot guarantee that a device is going to be compromised, but with enough data collected over time we can predict the likelihood of that device being attacked.
Certainly, that’s the way that attackers have been thinking. When Mirai hit in 2016, it took down a large DNS service provider, Rutgers University and even the entire country of Liberia with DDoS attacks that eclipsed the flood power of anything previously recorded. It achieved this record by strapping together legions of weak IP cameras and home routers into some of the most powerful botnets ever conceived. It did this with the rather paltry method of guessing a targeted devices password out of a tiny library of commonly used credentials. Once it had enslaved the device, it would search for other nearby devices that were similarly vulnerable.
Such devices are easy prey for a cyber criminal. A study by the SANS institute in 2017 showed that it only took two minutes for a device to be attacked once it was connected to the internet.
For an AI engine derived from Machine Learning algorithms to learn what will or won’t be malicious, masses of data will have to be acquired over time. The AI will literally have to learn along with the development of the IoT. As we fix old problems and develop new ones, utilizing AI like this one will learn along with it.
DigiCert Labs will be paying attention to the development of AI-based approaches, pattern recognition and network data consumption categorization that analyze the behavior of different IoT devices in a variety of environments.
When it comes to the IoT, like with all technology, we have to continue to evolve our thinking around security. AI is one to watch.
Avesta Hojjati is the head of R&D at DigiCert, where he manages advanced development of cyber security products. Before joining DigiCert, he was part of the Symantec and Yahoo security teams, as well as operating his own cyber security startup.
Avesta focuses on applied cryptography, blockchain, post-quantum crypto, and IoT security. He earned his Masters in computer science from University of Illinois at Urbana Champaign, and is currently completing his PhD dissertation.
About the Author(s)
You May Also Like

.jpg?width=700&auto=webp&quality=80&disable=upscale)
.jpg?width=700&auto=webp&quality=80&disable=upscale)
.jpg?width=700&auto=webp&quality=80&disable=upscale)
.jpg?width=300&auto=webp&quality=80&disable=upscale)
.jpg?width=300&auto=webp&quality=80&disable=upscale)
.jpg?width=300&auto=webp&quality=80&disable=upscale)
.jpg?width=300&auto=webp&quality=80&disable=upscale)
.jpg?width=300&auto=webp&quality=80&disable=upscale)